Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

A survey of cyber security threats and solutions for UAV

Security Threats at OSI layers

Cyber security breakdown: The OSI model
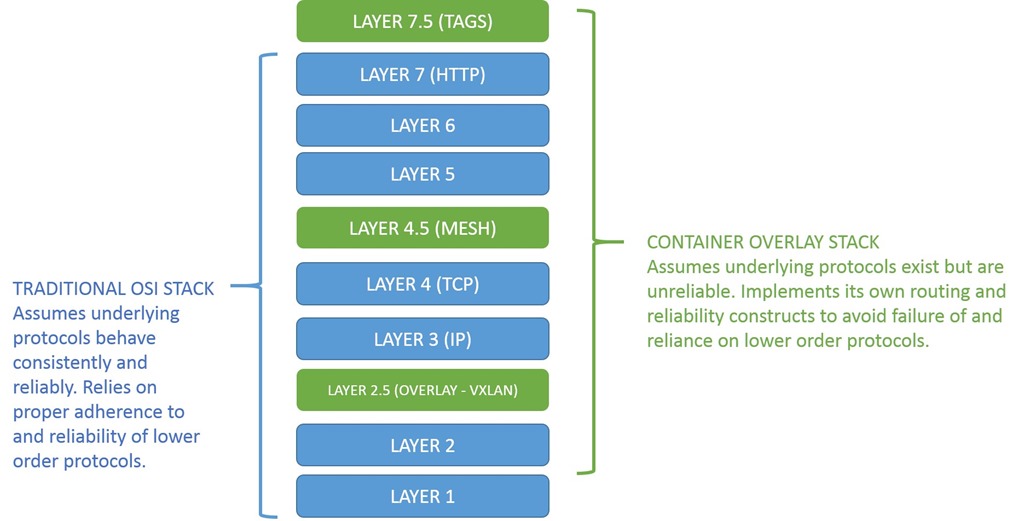
The New OSI Network Stack: Containers and Half-Layers
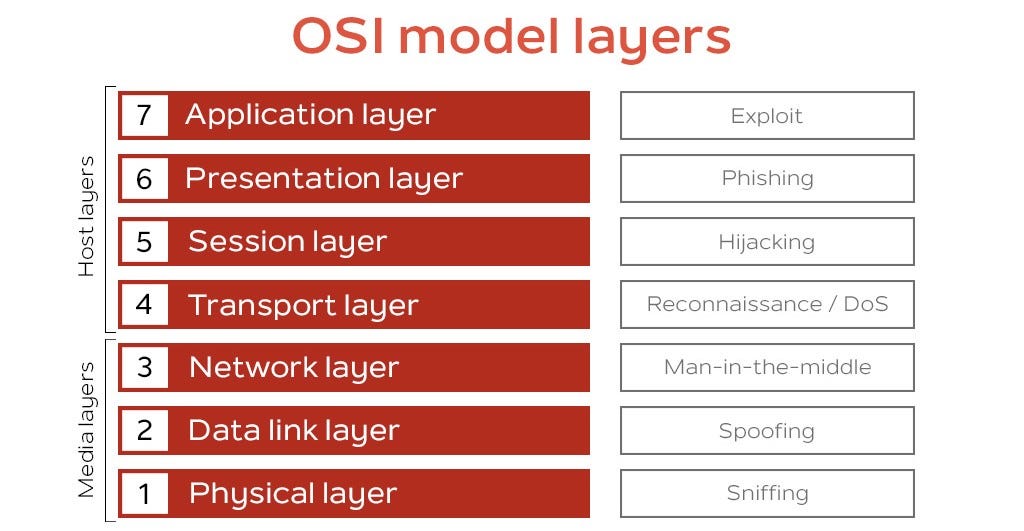
Cyberattacks On The OSI Layers, by MSBJ
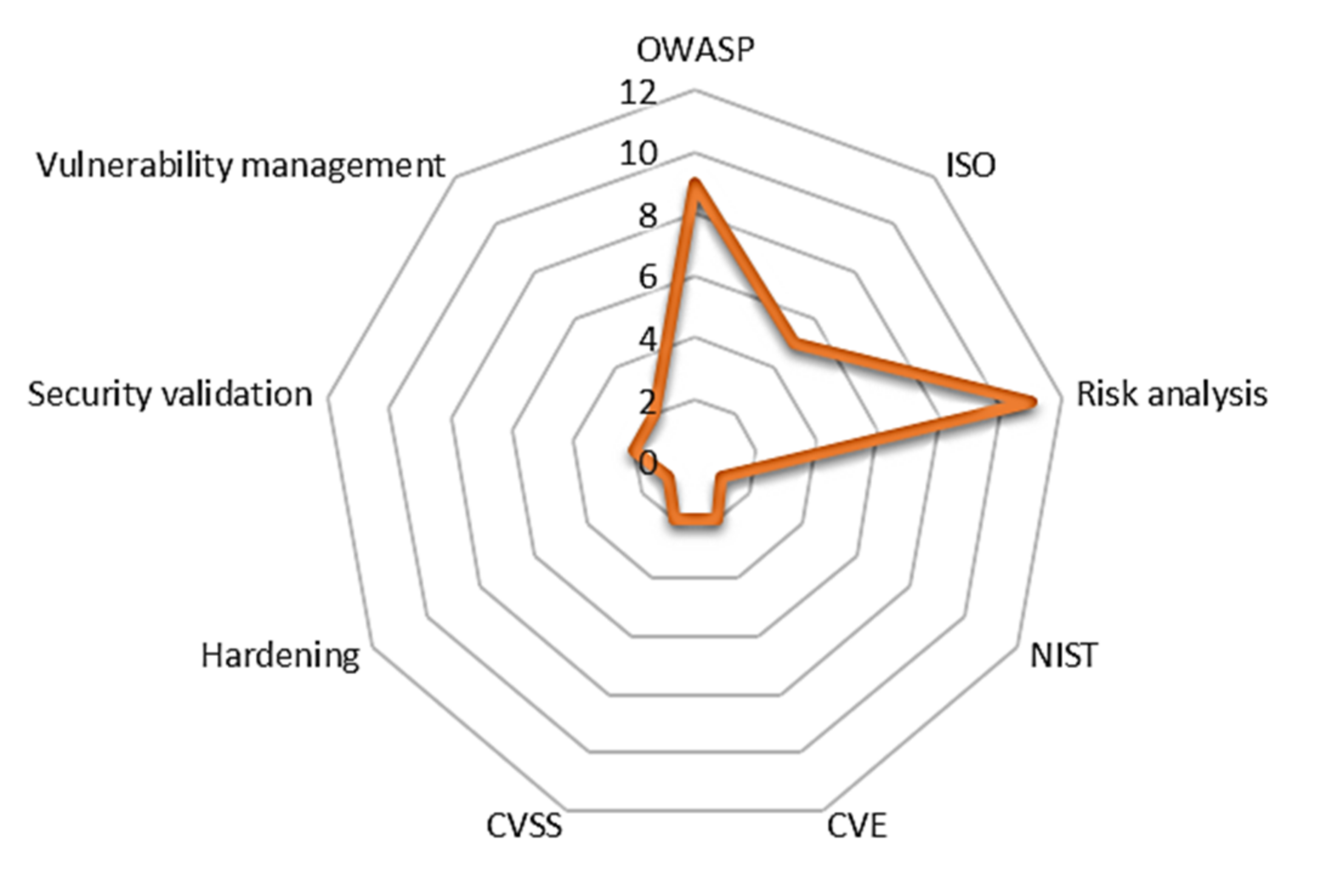
Applied Sciences, Free Full-Text
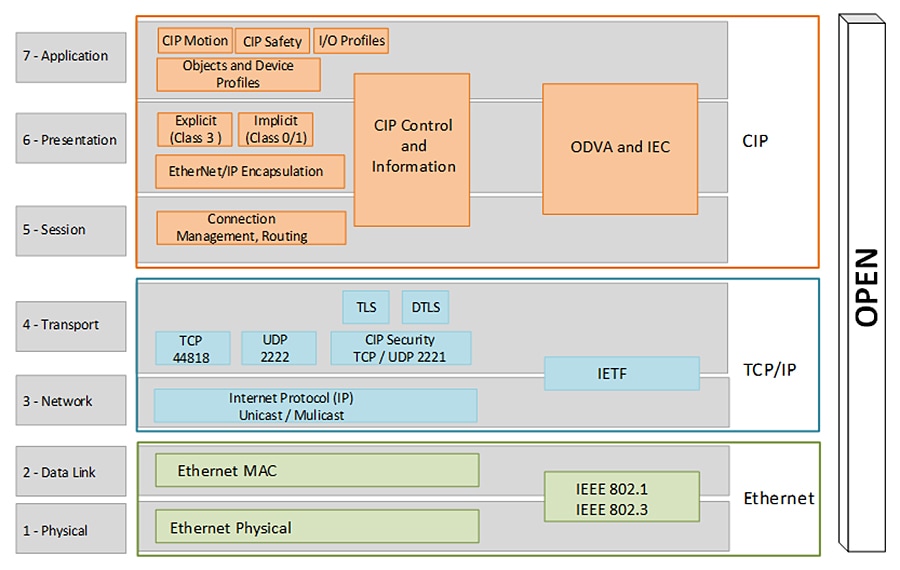
Deploying CIP Security within a Converged Plantwide Ethernet
How VMware can Secure Mobile Endpoints with Threat Defense (MTD
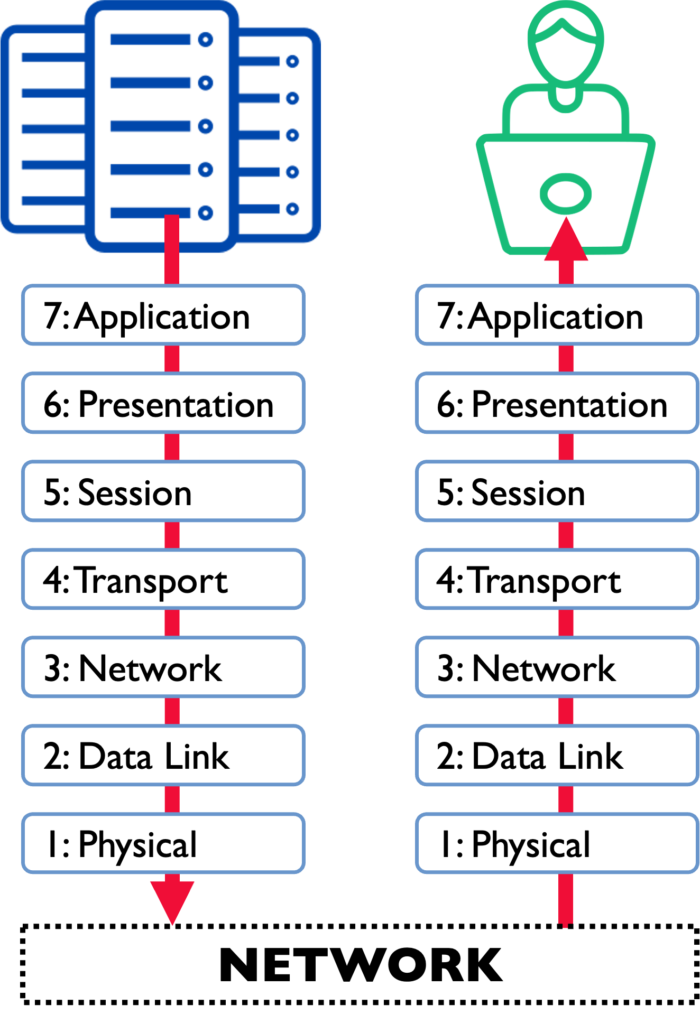
What Is the OSI Model, and How Can We Protect Its Critical Layers

Security Threats at OSI layers

Security Threats at OSI layers
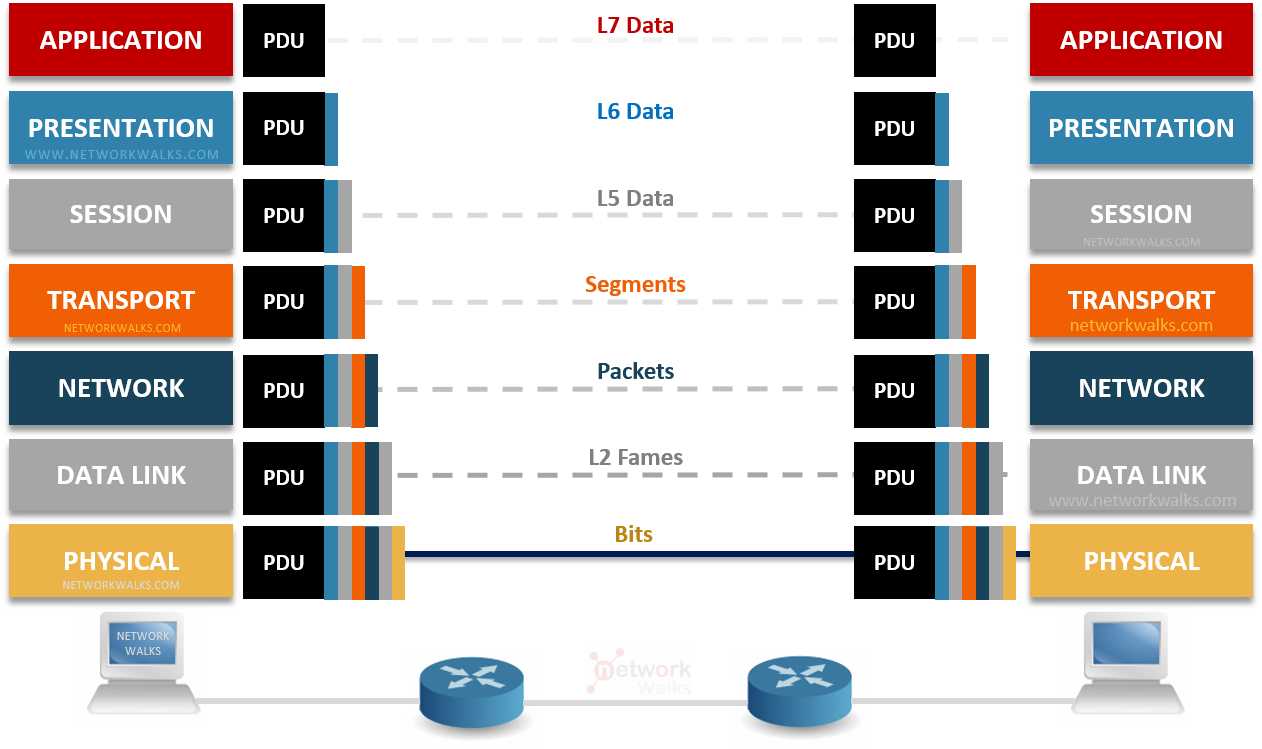
OSI Model (Open Systems Interconnection Model)

The OSI Model Explained in Easy Steps

The OSI model and cyber attack examples, originally published in
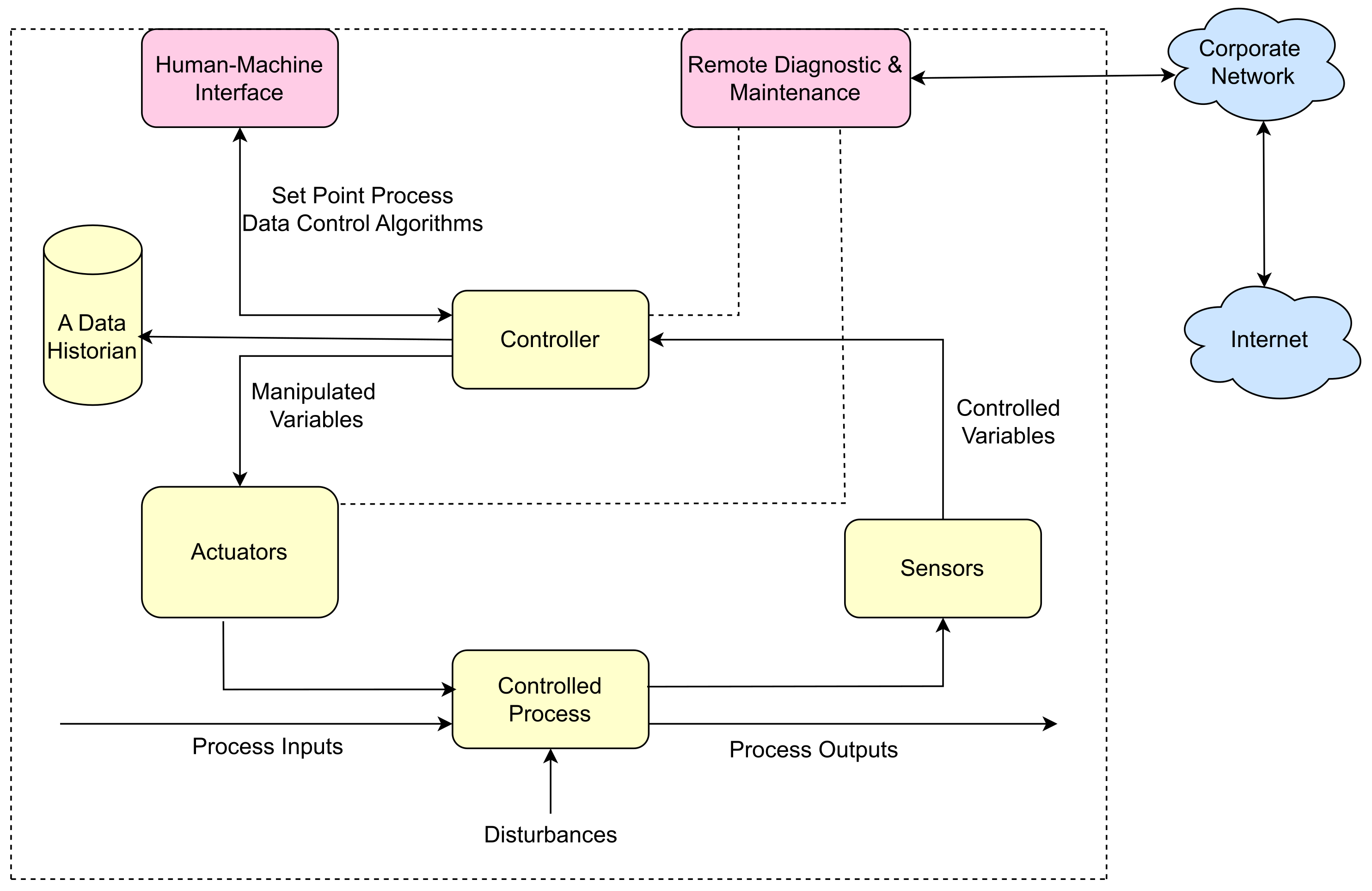
Sensors, Free Full-Text